If You Skip the Microsoft Account Sign-In During Windows 11 Home Setup, It Will Skip Protecting Your Drive Encryption Key
Blissful Ignorance
When I did a fresh install of Windows 11 Home on one of my PCs, I used one of the unofficial, unsupported, yet well known and commonly used tricks to get through the setup process without having to sign in with a Microsoft account. I set up my login to use a PIN1. I assumed this meant that the drive would then be encrypted and protected by Trusted Platform Module (TPM) integrity verification and backed by my PIN.
Et Tu Satya?
This turns out to be wrong.
It turns out that if you skip the Microsoft account sign-in step and only create a “local account”, your data is encrypted but the encryption key is stored on the drive unprotected. This unexpected-to-me behavior is cataloged deep in Microsoft’s own documentation:
[Device] encryption is enabled automatically so that the device is always protected. […] As part of [the out-of-box experience] preparation, device encryption is initialized on the OS drive and fixed data drives on the computer with a clear key that is the equivalent of standard BitLocker suspended state. […] If a device uses only local accounts, then it remains unprotected even though the data is encrypted
Okay, so what exactly does it mean if we are in this state? Well, the documentation above says that it “is the equivalent of standard BitLocker suspended state”, and Microsoft’s BitLocker documentation clarifies what this means:
Suspension of BitLocker does not mean that BitLocker decrypts data on the volume. Instead, suspension makes key used to decrypt the data available to everyone in the clear. New data written to the disk is still encrypted.
So, leaving the key in this “unprotected” or the encryption in means basically leaving the data on the drive unprotected. Any thief or whoever that gets their hands on your drive can get into your data by just decrypting it using the key sitting next to the encrypted data, “unprotected”.

Putting an encryption key on a drive right next to the data it encrypts is about as secure as a safe with the combination written right on it.
Read the Fine Print
I also want to return to the documentation above about the local encryption leaving the key unprotected, because it claims that there should be a warning when this happens:
As part of [the out-of-box experience] preparation, device encryption is initialized on the OS drive and fixed data drives on the computer with a clear key that is the equivalent of standard BitLocker suspended state. In this state, the drive is shown with a warning icon in Windows Explorer. The yellow warning icon is removed after the TPM protector is created and the recovery key is backed up.
For the record, I never noticed a yellow warning icon in my day to day use. That said, I personally find spotting an error indicator on Windows is like playing grandmaster level Where’s Waldo. So for this post, I went back through the process to actively look for it. Nothing shows up on the File Explorer page for the drive, where I would expect it.
Instead, I finally found it buried two levels deep in the Settings app, under “Privacy & security” > “Device encryption”.
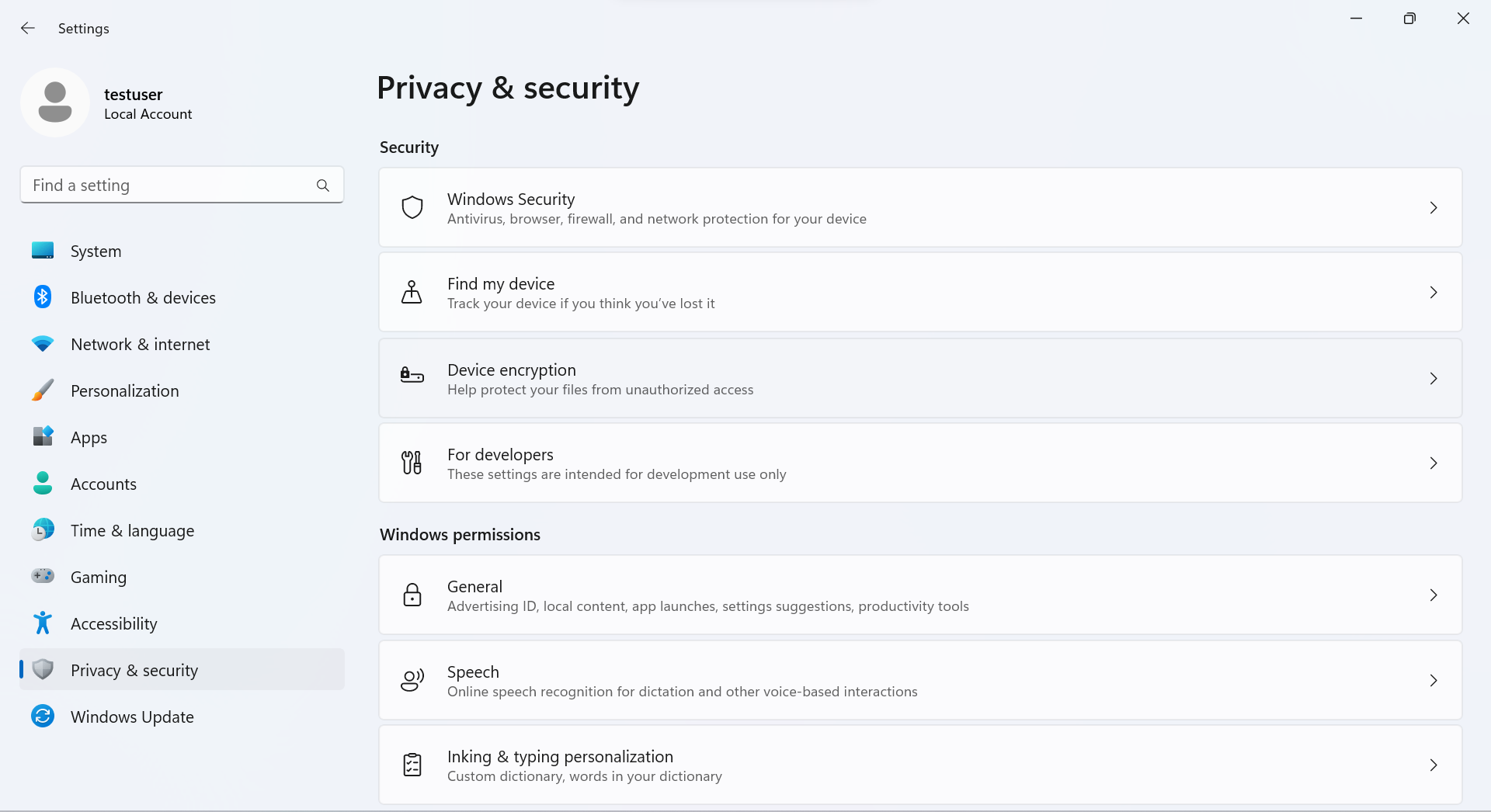
It shows up as a yellow bar that says “Sign in to your Microsoft account to finish encrypting this device.” I am not a huge fan of this wording, which might be read to imply that some of your data is already protected, especially when coupled with the fact that the “Device encryption” slider shows as “On”. Really, none of it is protected, because the key is unprotected.

Forewarned is Forearmed
I’m assuming that if you didn’t want to sign into a Microsoft account during setup, you probably don’t want to link your drive encryption key to your Microsoft account. If you are okay with doing that, I assume you can go ahead and tap the button in the warning and sign in to enable encryption.
So, to do that, we have to dive further into the world of unofficial, unsupported solutions with the manage-bde command line tool. Despite being named after the full featured, name brand BitLocker used in Windows 11 Pro, it works just fine on the more restricted, store brand “device encryption” we are stuck with in Windows 11 Home.
To dig in, run manage-bde -status in a shell like Command Prompt or PowerShell:
PS C:\Windows\system32> manage-bde -status
BitLocker Drive Encryption: Configuration Tool version 10.0.22621
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Disk volumes that can be protected with
BitLocker Drive Encryption:
Volume C: [OS]
[OS Volume]
Size: 1337.42 GB
BitLocker Version: 2.0
Conversion Status: Used Space Only Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 128
Protection Status: Protection Off
Lock Status: Unlocked
Identification Field: Unknown
Key Protectors: None Found
If you get an output like the one above, where it says that the drive is 100% encrypted, but that the “Protection Status” is “Protection Off” and lists no “Key Protectors”, it means you are in this unprotected state where your key is being stored in plaintext right next to your encrypted data. It’s a two-step process to enable key protection from this point.
First, you need to pick a protection scheme and then add a protector with some command like this:
PS C:\Windows\system32> manage-bde c: -protectors -add -tpm
BitLocker Drive Encryption: Configuration Tool version 10.0.22621
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Key Protectors Added:
TPM:
ID: {XXXXX-XXXXX-XXXXX-XXXXX-XXXXXXXXXXX}
PCR Validation Profile:
7, 11
(Uses Secure Boot for integrity validation)
You can find more information about supported key protection schemes here. Unfortunately, my preferred most secure options I tried gave licensing errors, and are thus presumably only available on a more fully equipped version of Windows with the full version of BitLocker.
No matter what other key protectors you add, you should also add a recovery key. This is so that you can still decrypt your data if something goes wrong with your main key protector. You can do this by calling something like manage-bde c: -protectors -add -recoverypassword. You then save the key it gives you in a safe place.2
Second, you need to enable the protection on that specific drive. This is done with another manage-bde command:
PS C:\Windows\system32> manage-bde -on C:
BitLocker Drive Encryption: Configuration Tool version 10.0.22621
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Volume C: [OS]
[OS Volume]
NOTE: This command did not create any new key protectors. Type
"manage-bde -protectors -add -?" for information on adding more key protectors.
NOTE: Encryption is already complete.
Turned on BitLocker protection by enabling key protectors.
After you complete both steps, you can repeat the status check to confirm it worked. If everything is right, it will look like this:
PS C:\Windows\system32> manage-bde -status
BitLocker Drive Encryption: Configuration Tool version 10.0.22621
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Disk volumes that can be protected with
BitLocker Drive Encryption:
Volume C: [OS]
[OS Volume]
Size: 1337.42 GB
BitLocker Version: 2.0
Conversion Status: Used Space Only Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 128
Protection Status: Protection On
Lock Status: Unlocked
Identification Field: Unknown
Key Protectors:
TPM
Now my key is stored in my TPM, which will only release it when its integrity checks pass. This is less protection than I would generally prefer, but still much more protection than earlier. It should make it hard enough for a garden variety thief to get their hands on my data if they steal my device. I doubt it would keep out a seriously motivated adversary, though. Unfortunately, as far as I can tell, I would have to pay extra to get full BitLocker for anything offering more protection.
Obligatory Ranting
At the surface level, I don’t think this corner case of systematically lowering the security of users who opt out of using Microsoft accounts was intentional. I think for many normal users having a default that data is not encrypted unless the key is backed up is a reasonable trade-off to avoid catastrophic data loss. Yet, I wonder: why didn’t the setup flow just ask me if I wanted to be responsible for backing up my key myself, or if I wanted to back it up with Microsoft? Apple does!
It’s the obvious answer to that question that pushes me towards my personal conclusion that at a deeper level this outcome was the inevitable product of an earlier deceit and coercion. Microsoft wants you to use use a Microsoft account. They think it makes you more likely to consume Microsoft services. So, they choose not to ask what you want, and instead push you along the path to what they want.
It’s easy to imagine what happens next. Once that decision was made, the standard physics of corporate software development sprung into action. Inevitably, no one prioritizes polishing the setup flow for the small portion of users that manage to jump through the hoops to go down the undesired path. It’s much simpler to silently conflate the choice about key backup with the choice of using a local account. If you use a local account, you don’t backup your keys, so you don’t get disk protection. Simple as.
Also, full BitLocker should really come standard. This kind of confusing, customer-hostile product segmentation was the butt of jokes from Steve Jobs himself 16 years ago. In today’s world of mobile devices, good encryption is table stakes. Charging extra for it feels like keeping seatbelts exclusive to Mercedes Benz. At this point I’m not paying for the upgrade to Pro for BitLocker out of spite, more than anything else.
Summary / TL;DR:
If you set up Windows 11 Home without a Microsoft account, you should double check that drive protection is actually turned on. By default, PCs set up with local accounts remain unprotected. Checking is best done by diving into the command line; turning on the protection if it’s off requires even more Windows command line time. Lucky you! Microsoft discourages setting up PCs with only local accounts, so I doubt they will change this behavior or make fixing this edge case easier.
Change Log
- 1/27/24: Original Post
- 1/27/24: Update with great feedback from @Rairii.
-
This is as far as I can tell, sadly, the highest level of protection available on Windows 11 Home for this device. If I want more, I’ll have to shell out extra bucks to get Windows 11 Pro and its’ full fat BitLocker. I might want more, because as @Rairii points out, TPM protection is pretty weak. ↩
-
Hat tip to @Rairii who pointed this out to me on Mastodon. ↩